Device Management
Overview
Section titled “Overview”Manage your organization’s device inventory, configurations, and lifecycle processes through ARROW’s comprehensive device management platform.
Device Lifecycle Overview
Section titled “Device Lifecycle Overview”The ARROW device lifecycle follows a structured flow from initial request through deployment and eventual return. Understanding this lifecycle helps you track device status and anticipate next steps.
flowchart TD
A[Device Request Created] --> B{Approved?}
B -->|No| C[Pending Review]
B -->|Yes| D[Device Assigned]
D --> E[Imaging Started]
E --> F[Device Ready]
F --> G[Shipment Created]
G --> H[In Transit]
H --> I[Delivered - On Site]
I --> J{Engagement Complete?}
J -->|No| I
J -->|Yes| K[Return Shipment]
K --> L[Device Returned]
L --> M[Request Completed]
M --> N[Device Cleanup]
N --> O[Device Available for Reuse]
Device Status Reference
Section titled “Device Status Reference”| Status | Description | User Actions Available |
|---|---|---|
pending | Request awaiting approval | View details, edit request |
approved | Request approved, device being assigned | Track assignment progress |
provisioning | Device being imaged and configured | Monitor build progress |
shipping | Shipment label created, awaiting pickup | View tracking info |
in-transit | Device in carrier network | Track shipment |
on-site | Device delivered and operational | Full device management |
returned | Device returned to warehouse | Await completion |
complete | Engagement finished, device cleaned | View archived details |
ARROW Portal - Devices
Section titled “ARROW Portal - Devices”Once a device is provisioned, it will show up within the Devices page of the ARROW Portal. The default view places each device in a card-style layout. This can be changed to list view by selecting the List View Icon. The Devices page displays comprehensive information organized from the upper left downwards:
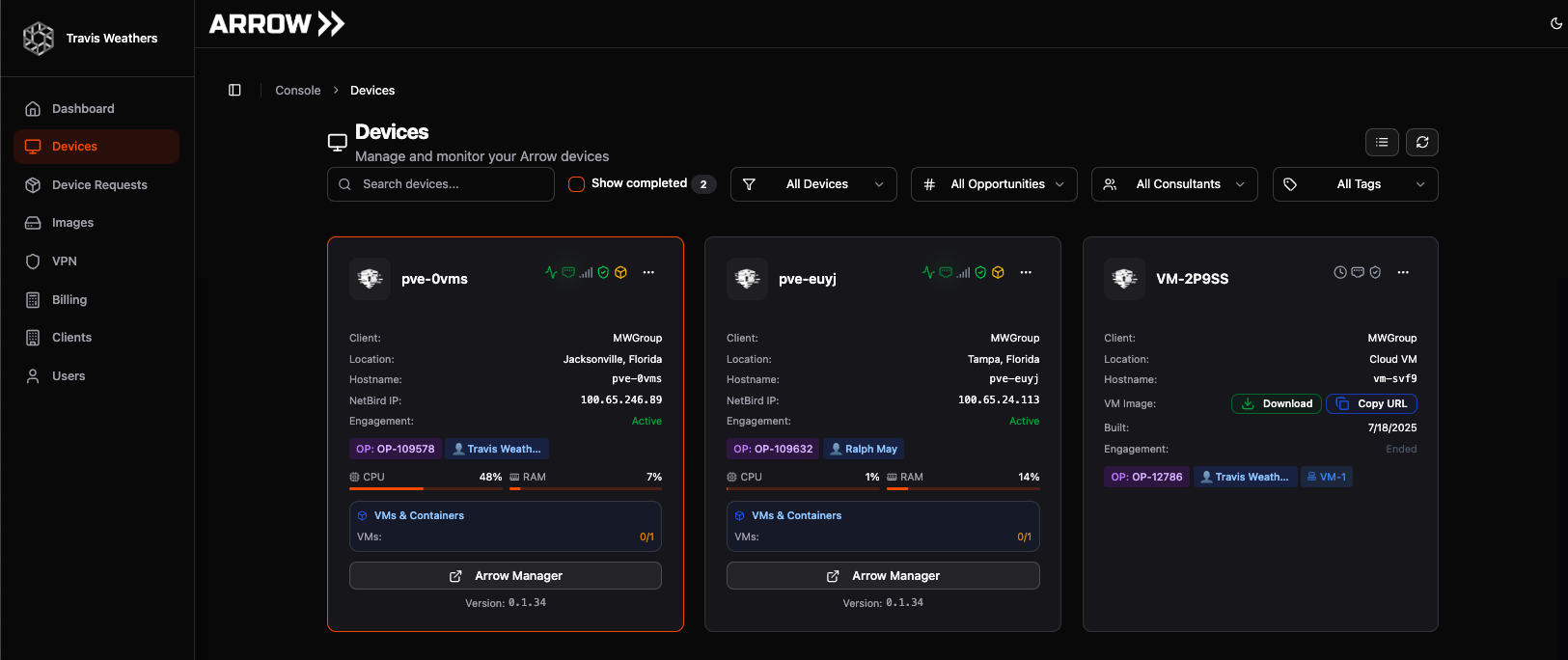 Devices Card View
Devices Card View
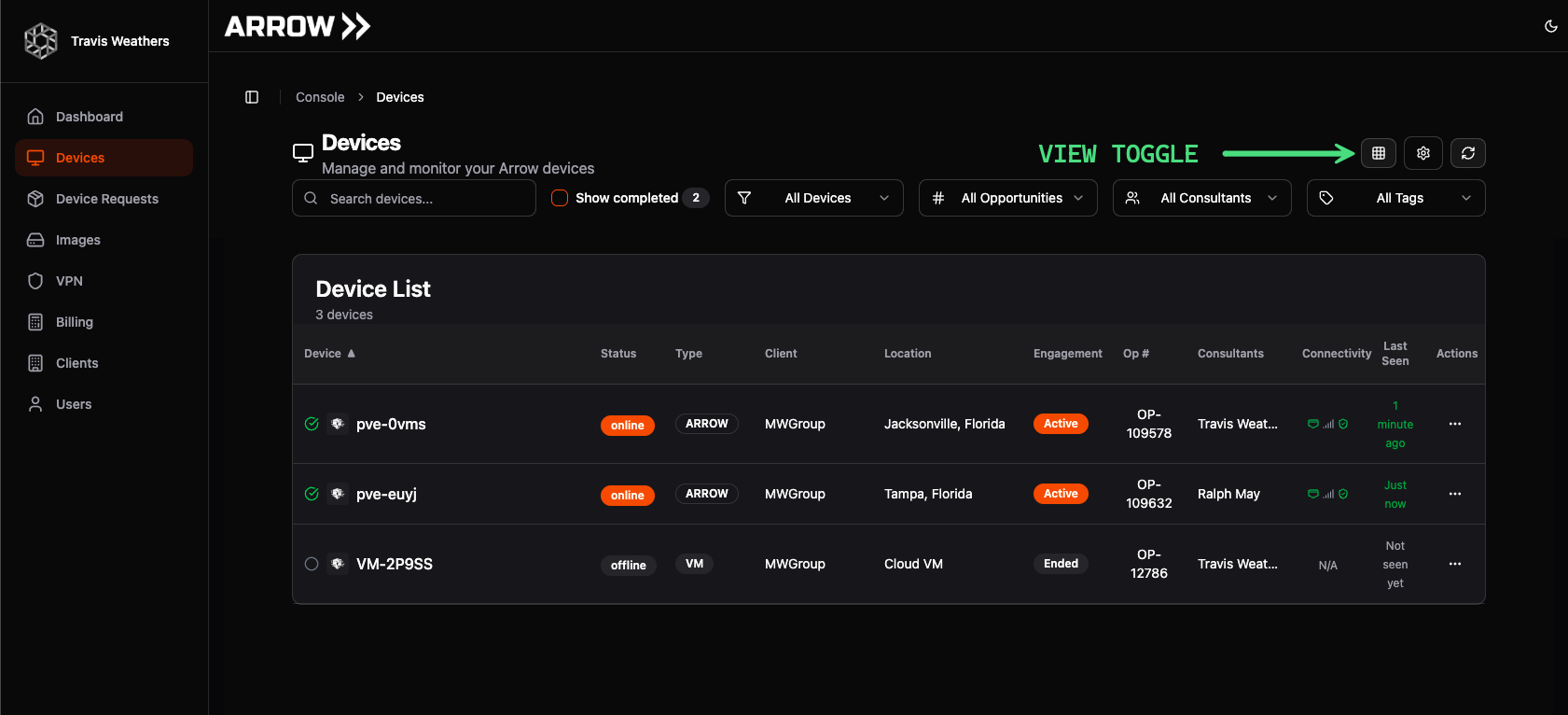 Devices List View
Devices List View
Device Overview Elements
Section titled “Device Overview Elements”| Element | Description |
|---|---|
| Client Logo | Added for aesthetic recognition during the client onboarding process |
| Unique Device Name | Randomly generated device/hostname set during the provisioning process |
Device Status Icons
Section titled “Device Status Icons”
| Status | Icon | Description |
|---|---|---|
| Health Monitor | Heartbeat | Indicates metrics health. Device metrics are pulled every minute - keep this in mind during troubleshooting |
| Primary Adapter | Ethernet port | Shows if the device is connected via Ethernet (primary connection) |
| Failover Adapter | Signal strength | Indicates if the device is in failover mode and connected via cellular |
| VPN Status | Shield check | Shows whether the device has a stable VPN connection |
| Virtual Machine Status | Cube | Indicates if a virtual machine is deployed and its health status |
Device Actions Menu
Section titled “Device Actions Menu”The ellipsis menu provides access to the following actions:
| Action | Description |
|---|---|
| View Details | Open the device details view to see full metrics, interfaces, and recent activity |
| Access Arrow Manager | Launch the ARROW Manager UI for live administration on the device |
| Edit Tags | Add, remove, or rename tags used for search and grouping |
| Edit Request Details | Update the originating device request (notes, dates, consultants) |
| Copy Arrow Password | Copy the ARROW Manager/user password to your clipboard |
| Copy Root Password | Copy the device’s root credential to your clipboard |
| Request VPN Setup Token | Generate a one-time VPN setup token |
Device Request Workflow
Section titled “Device Request Workflow”Device requests initiate the device lifecycle and track the entire engagement process. Users can create, search, and manage requests through the portal.
Creating Device Requests
Section titled “Creating Device Requests”When creating a device request, you’ll specify:
- Client/Organization: The target organization for the device
- Device Specification: Hardware configuration required
- Engagement Dates: Start and end dates for the engagement
- Consultants: Assigned team members
- Shipping Address: Delivery destination with contact information
Searching and Filtering
Section titled “Searching and Filtering”The device requests view supports filtering by:
- Organization name
- Client name
- Consultant assignment
- Tracking number
- Device serial number
- Request status
Complementary (Comp) Status
Section titled “Complementary (Comp) Status”Requests can be marked as “comp” (complementary) for no-charge device deployments. This status affects billing and reporting but does not change the device workflow.
sequenceDiagram
participant User
participant Portal as ARROW Portal
participant Backend
participant NetBird as NetBird VPN
participant Device
User->>Portal: Create Device Request
Portal->>Backend: Submit Request
Backend->>Backend: Generate Credentials
Backend->>NetBird: Create VPN Setup Key
NetBird-->>Backend: Setup Key
Backend-->>Portal: Request Created
Portal-->>User: Request Confirmation
User->>Portal: Approve Request
Portal->>Backend: Update Status to Approved
Backend->>Backend: Assign Device
Backend->>Backend: Create Device Settings
Backend-->>Portal: Device Assigned
Backend->>Device: Trigger Imaging
Device->>Backend: Report Build Progress
Backend-->>Portal: Update Status
Portal-->>User: Device Ready
Device Settings and Configuration
Section titled “Device Settings and Configuration”Each provisioned device has configurable settings managed through the portal and ARROW Manager.
Device Credentials
Section titled “Device Credentials”| Credential Type | Purpose | Access Method |
|---|---|---|
| ARROW Manager Password | Login to ARROW Manager dashboard | Copy from device card action menu |
| Root Password | Administrative access to device | Copy from device card action menu |
| VPN Setup Token | One-time token for VPN enrollment | Request from device card action menu |
Device Tags
Section titled “Device Tags”Tags help organize and search for devices across your fleet:
- Add custom tags for project identification
- Use tags for filtering in the device list
- Tags persist throughout the device lifecycle
Device Licensing
Section titled “Device Licensing”ARROW Control licensing enables advanced features on your devices. Licenses are managed per-device and control feature availability.
License Features
Section titled “License Features”| Feature | Description |
|---|---|
| VNC Access | Remote desktop access to virtual machines |
| Application Control | Manage installed applications remotely |
| Remote Access | Full remote administration capabilities |
| Monitoring | Real-time metrics and health monitoring |
| Advanced Security | Enhanced security controls and policies |
Licenses are valid for 365 days from activation and can be renewed through the portal.
Device Location Tracking
Section titled “Device Location Tracking”ARROW tracks device location through multiple sources to provide accurate geographic information:
| Source | Priority | Description |
|---|---|---|
| GPS Tracking | Highest | Hardware GPS when available |
| Shipping Address | High | Address from device request |
| IP Geolocation | Standard | Location based on public IP address |
Location data is cached and updated periodically to balance accuracy with performance.
Device Lookup
Section titled “Device Lookup”For PXE boot scenarios, devices can be discovered via MAC address lookup. This enables:
- Automatic device identification during network boot
- Matching physical devices to pending requests
- Streamlined inventory and imaging workflows
See Auto-Inventory for details on the automated inventory collection process.
Device & Engagement Information
Section titled “Device & Engagement Information”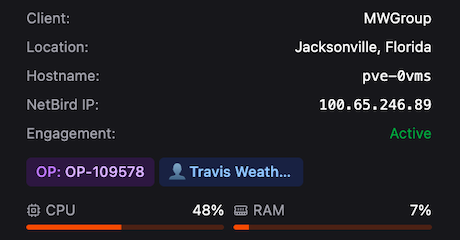
| Field | Description |
|---|---|
| Client | The corresponding client organization |
| Location | Location data pulled from various sources including IP geolocation and shipping address |
| Hostname | Matches the Unique Device Name. Format: PVE (Proxmox Virtual Environment) + four-digit string. Full VPN hostname: hostname.arrow.local |
| NetBird IP | IP address assigned by the NetBird VPN orchestrator |
| Engagement Status | Status driven by dates defined in the request. View completed devices using Show completed in the Devices page header |
| OP & Consultants | Optional organizational data such as project numbers and assigned consultants |
| CPU & RAM | Current load statistics and resource usage for the device |
Virtual Machine Field
Section titled “Virtual Machine Field”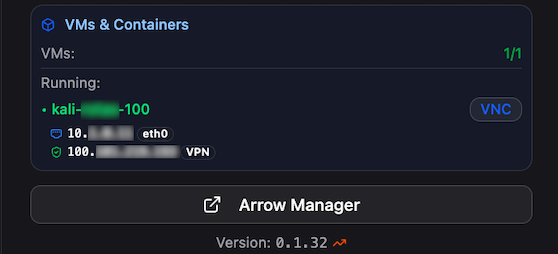
| Field | Description |
|---|---|
| VMs & Containers | Details for running virtual machines including hostname, internal IP, and VPN IP. Includes direct link to NoVNC HTML5 interface (fast, auto-scalable, with copy/paste support) |
| ARROW Manager Button | Opens the ARROW Manager application running on the physical device |
ARROW Manager - Device Setup
Section titled “ARROW Manager - Device Setup”To set up a physical device for testing, click on the ARROW Manager button in the device card. This will launch a new browser tab that connects to the ARROW Manager application running on the device. This dashboard is available via the VPN connection (Ethernet or Cellular) and via the WiFi Hotspot for client configuration. To log in to the dashboard, click the Login to Dashboard button with the following credentials:
- Username: manager@localhost.com
- Password: ARROW Password supplied in the device card (Action Menu)
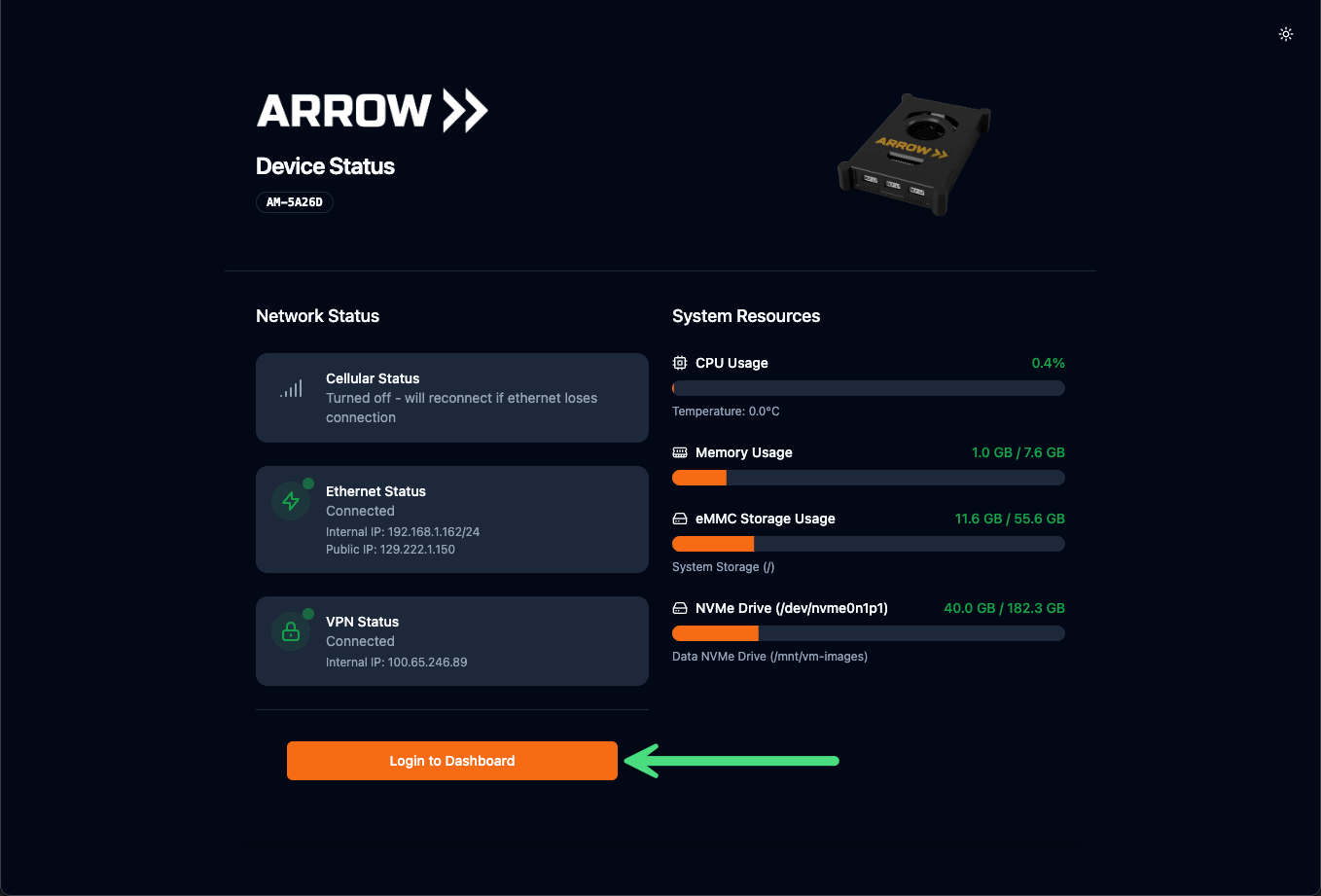 ARROW Manager Dashboard Login Screen
ARROW Manager Dashboard Login Screen
To get started with testing you need to do the following:
- Set a LUKS Encryption Key which will encrypt a portion of the NVMe drive
- Deploy a Virtual Machine from the AppLibrary
- (Optional) Attach any USB devices (e.g., wireless cards) to the virtual machine
Setting a Static IP Address (Physical Device)
Section titled “Setting a Static IP Address (Physical Device)”We always recommend having your client assign a Static IP address via DHCP issuance within their networking equipment. However, you or your client can manually assign a static IP address by navigating to the Network Settings page, selecting the Static IP radio button, and supplying the desired values. No reboot is required as the arrow-network-manager service will detect the changes and will automatically attempt to bring up the VPN connection on the primary interface (Ethernet). If the Static IP address details are entered incorrectly or there are security controls in place blocking egress or the VPN Orchestrator host, the device will fail back over to cellular or the WiFi Hotspot.
IMPORTANT Please do not make direct edits to
/etc/network/interfaceswithout first consulting the ARROW support team. All network configurations should be performed exclusively via the Settings tab within the ARROW Manager portal.
The following is a sample output of the /etc/network/interfaces file when the Proxmox device is set to DHCP and Static IP addressing as well as the standard contents of the wwan0 (cellular modem) and wlo1 (wireless hotspot) files. There should never be a use case where the wwan0 and wlo1 files need modification.
Static IP Configuration - /etc/network/interfaces
# <-SNIPPED FOR BREVITY->
auto loiface lo inet loopback
auto enp2s0iface enp2s0 inet manual
iface wlo1 inet manual
iface wlx00c0cab2f4b8 inet manual
iface wwan0 inet manual
auto vmbr0iface vmbr0 inet static address 192.168.1.55/24 gateway 192.168.1.1 bridge-ports enp2s0 bridge-stp off bridge-fd 0 bridge-vlan-aware yes bridge-vids 2-4094#Managed by Arrow Manager
source /etc/network/interfaces.d/*DHCP Configuration - /etc/network/interfaces
# <-SNIPPED FOR BREVITY->
auto loiface lo inet loopback
auto enp2s0iface enp2s0 inet manual
iface wlo1 inet manual
iface wlx00c0cab2f4b8 inet manual
iface wwan0 inet manual
auto vmbr0iface vmbr0 inet dhcp bridge-ports enp2s0 bridge-stp off bridge-fd 0 bridge-vlan-aware yes bridge-vids 2-4094#Managed by Arrow Manager
source /etc/network/interfaces.d/*Cellular Configuration - /etc/network/interfaces.d/wwan0
# <-SNIPPED FOR BREVITY->
# WWAN0 LTE interface configurationallow-hotplug wwan0iface wwan0 inet manual dns-nameservers 8.8.8.8 8.8.4.4 1.1.1.1
# Disable IPv6 on this interface post-up echo 1 > /proc/sys/net/ipv6/conf/wwan0/disable_ipv6Hotspot Configuration - /etc/network/interfaces.d/wlo1
# <-SNIPPED FOR BREVITY->
auto wlo1iface wlo1 inet static address 10.123.45.1 netmask 255.255.255.0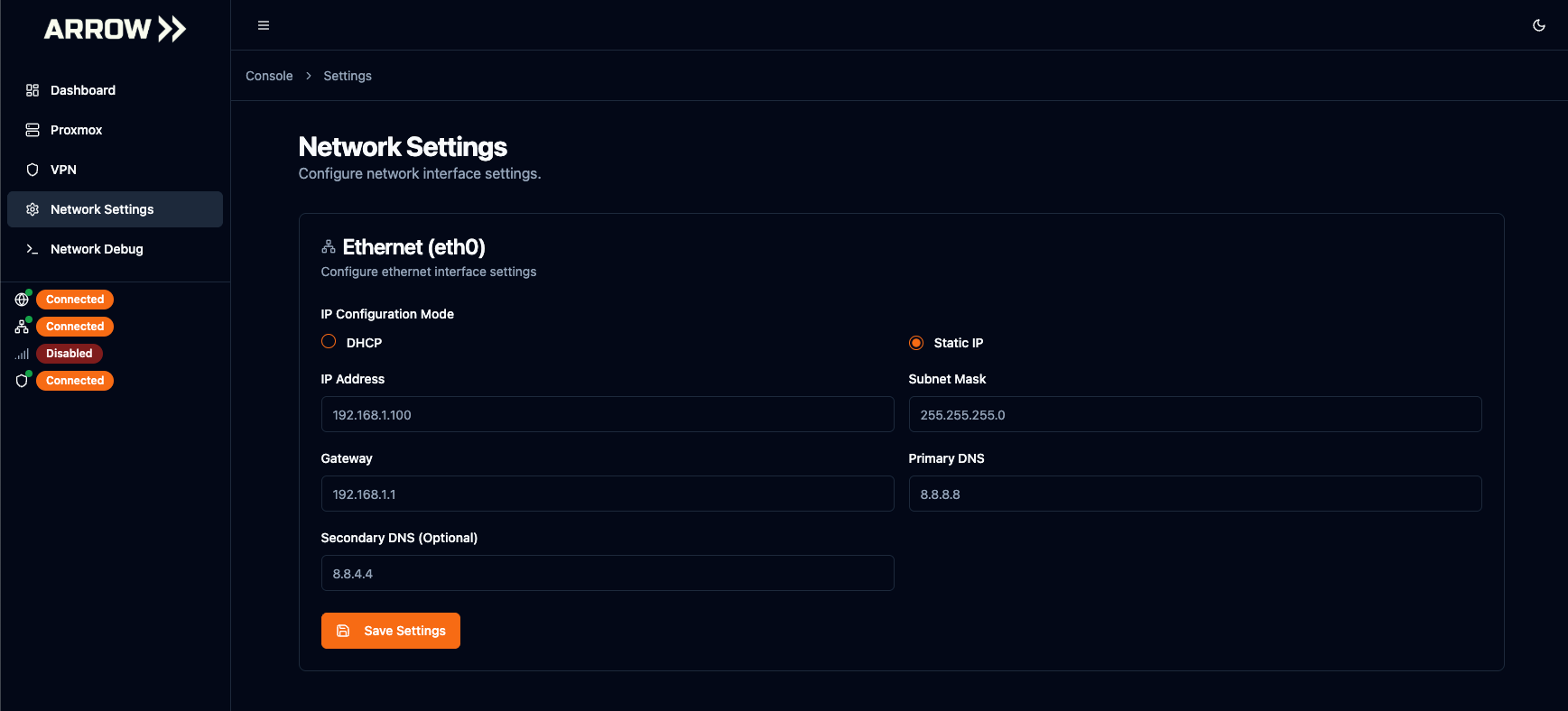 Static IP Assignment - Physical Device
Static IP Assignment - Physical Device
Setting up LUKS Encryption
Section titled “Setting up LUKS Encryption”Navigate to the Proxmox tab inside the ARROW Manager application. You will see a message stating “Encrypted Storage Setup Required”. Click on the Setup Encryption button, supply an encryption key that aligns with your organization’s policy, and click the Create Encrypted Storage button. It will take approximately 15-30 seconds for the encryption process to complete.
Important Ensure that you store the LUKS Encryption Key in a secure method that is approved by your organization. Should the device lose power or require a reboot, you will need to enter the encryption key to restart the virtual machine. VTEM Labs does not store the key and cannot assist in data/key recovery.
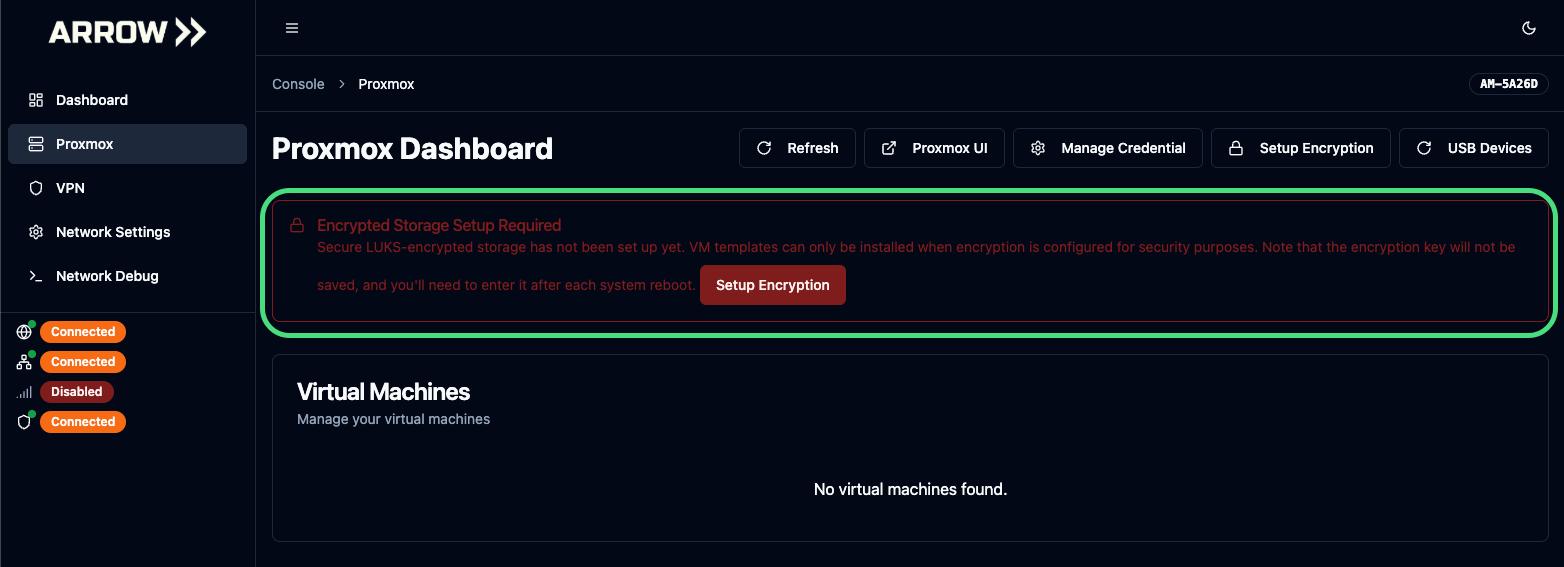 LUKS Setup Warning
LUKS Setup Warning
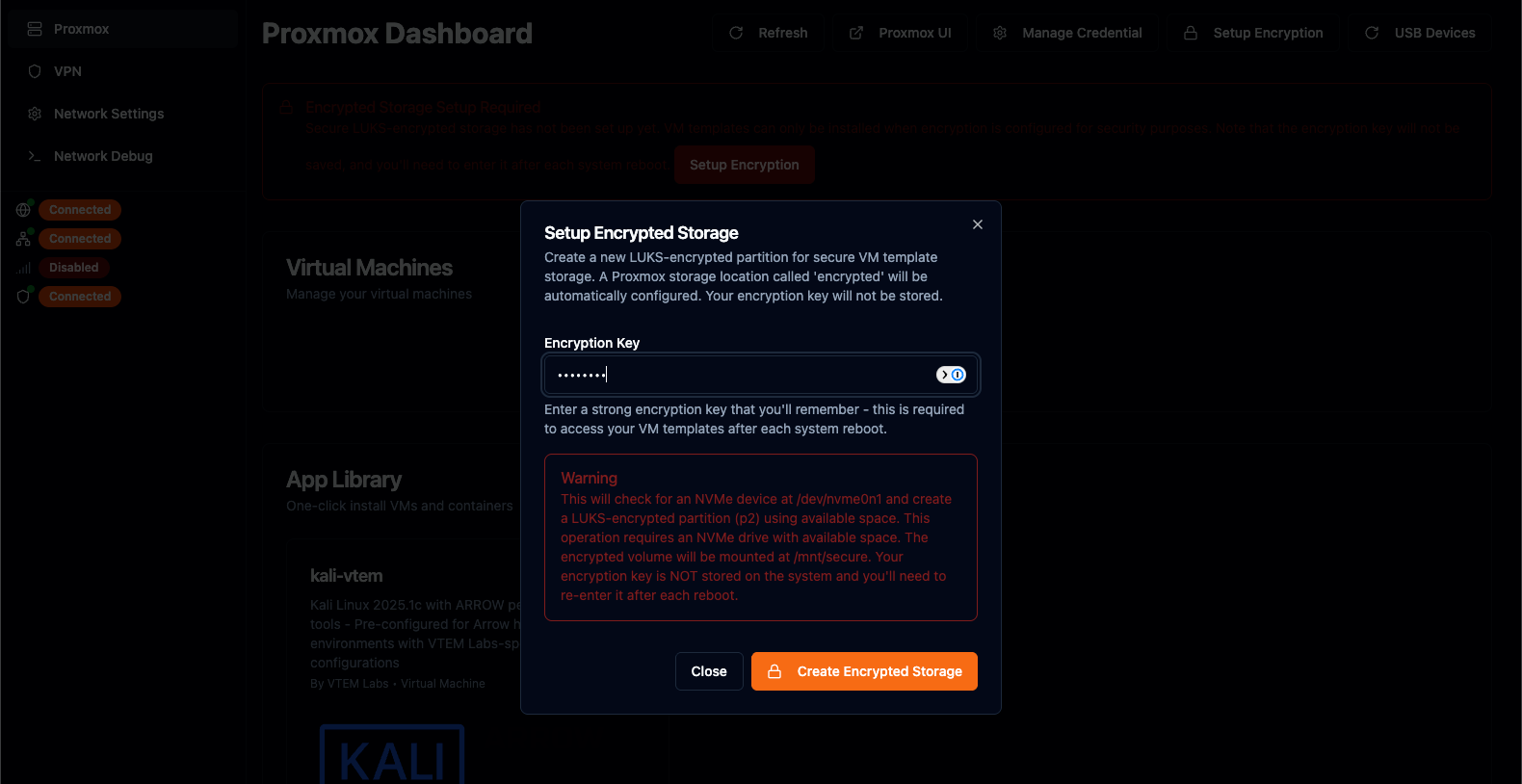 LUKS Key Setup
LUKS Key Setup
Once the encrypted NVMe partition has been created, you can now deploy a virtual machine.
Deploying a Virtual Machine
Section titled “Deploying a Virtual Machine”To deploy a virtual machine, select an image from the App Library and click the Deploy button. This will launch the Configure VM Deployment window. This process builds out the cloud-init configuration for when the Proxmox template file is deployed on the LUKS-encrypted partition.
Required Configuration Values:
Section titled “Required Configuration Values:”| Field | Description |
|---|---|
| Root Password | Password for the root user on the virtual machine |
| ARROW User Password | Password for the arrow user account on the virtual machine |
| VPN Setup Key | Key required to add the virtual machine to your VPN. Generate this from the Device Card on the ARROW Portal inside the (Action Menu) |
Optional Configuration Values:
Section titled “Optional Configuration Values:”| Field | Description |
|---|---|
| SSH Public Key | Enables SSH access to the ARROW and ROOT accounts without using defined passwords |
| Netbird Device Name | Custom device name that can be set in the VPN Setup menu |
| MAC Address | Custom MAC address for the virtual machine. Useful for providing clients with device MAC addresses in advance for NAC/IP address provisioning prior to device arrival |
| Static IP Configuration | Configure the virtual machine to use a static IP address |
Apply the desired settings and click the Create VM button. It will take approximately 50 seconds to fully deploy the virtual machine. If any USB devices are connected to the device, you will see the details of the device(s) and an Attach button. Attaching a device will induce a restart. The virtual machine will start sending statistics to the metrics server. However, the ARROW Portal only pulls this information every minute.
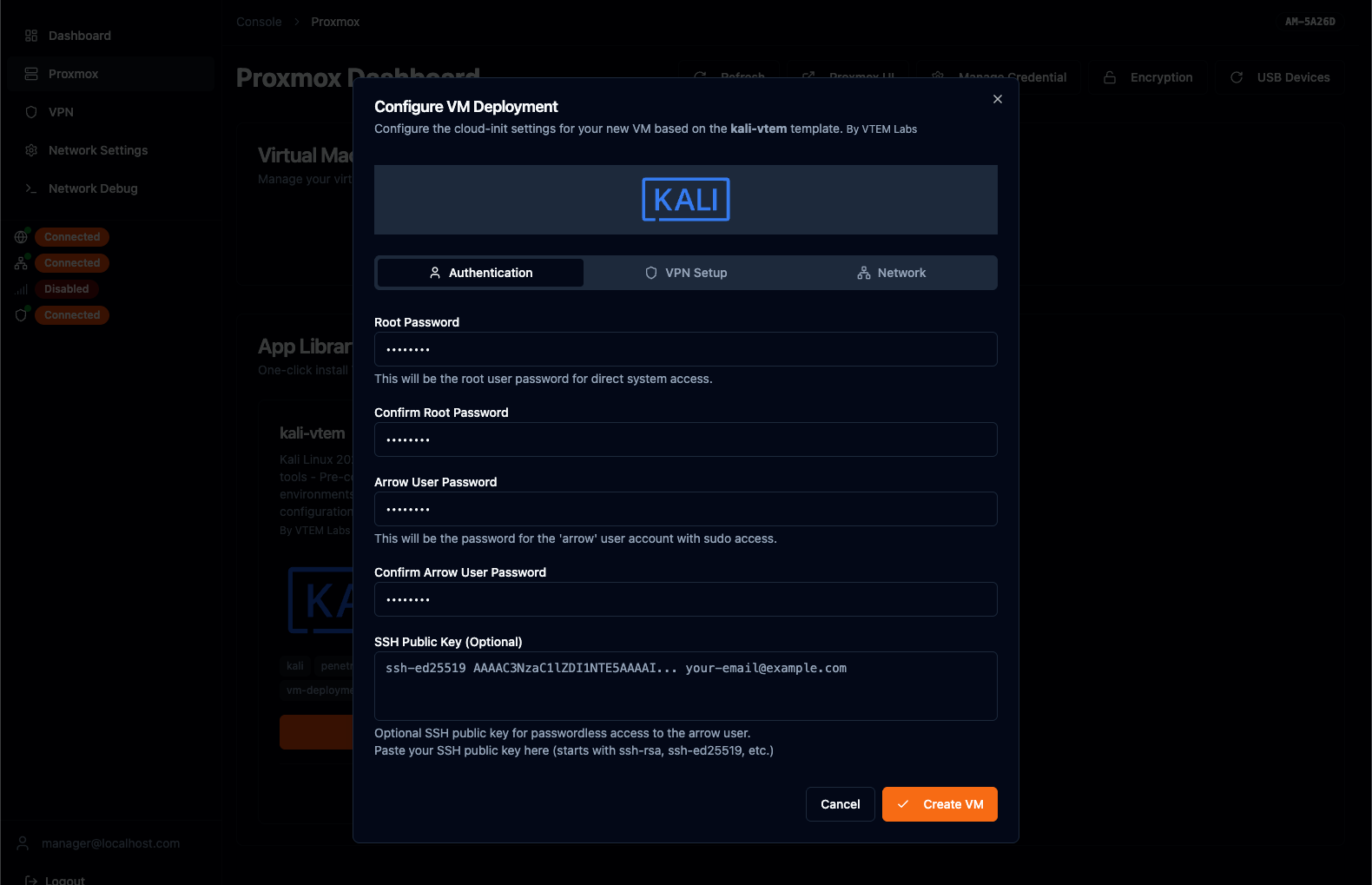 Configure VM Deployment Window
Configure VM Deployment Window
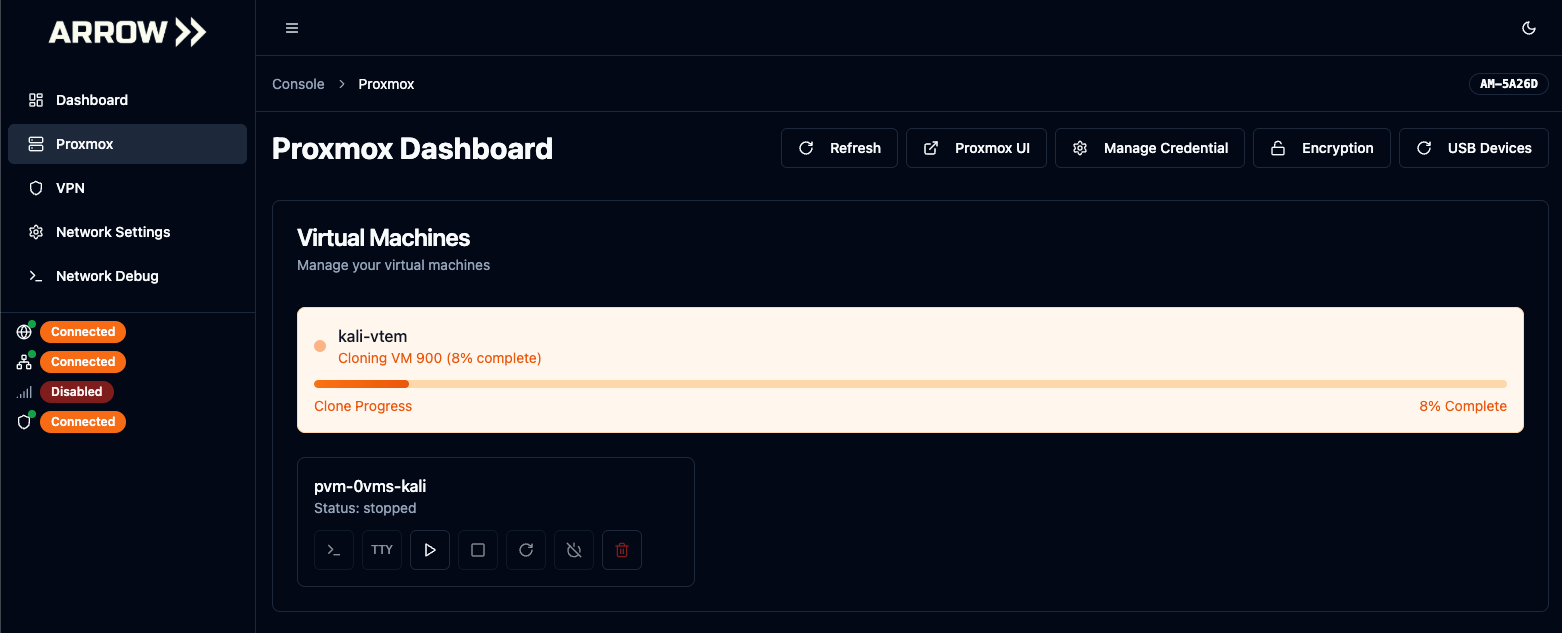 Virtual Machine Deployment Status Indicator
Virtual Machine Deployment Status Indicator
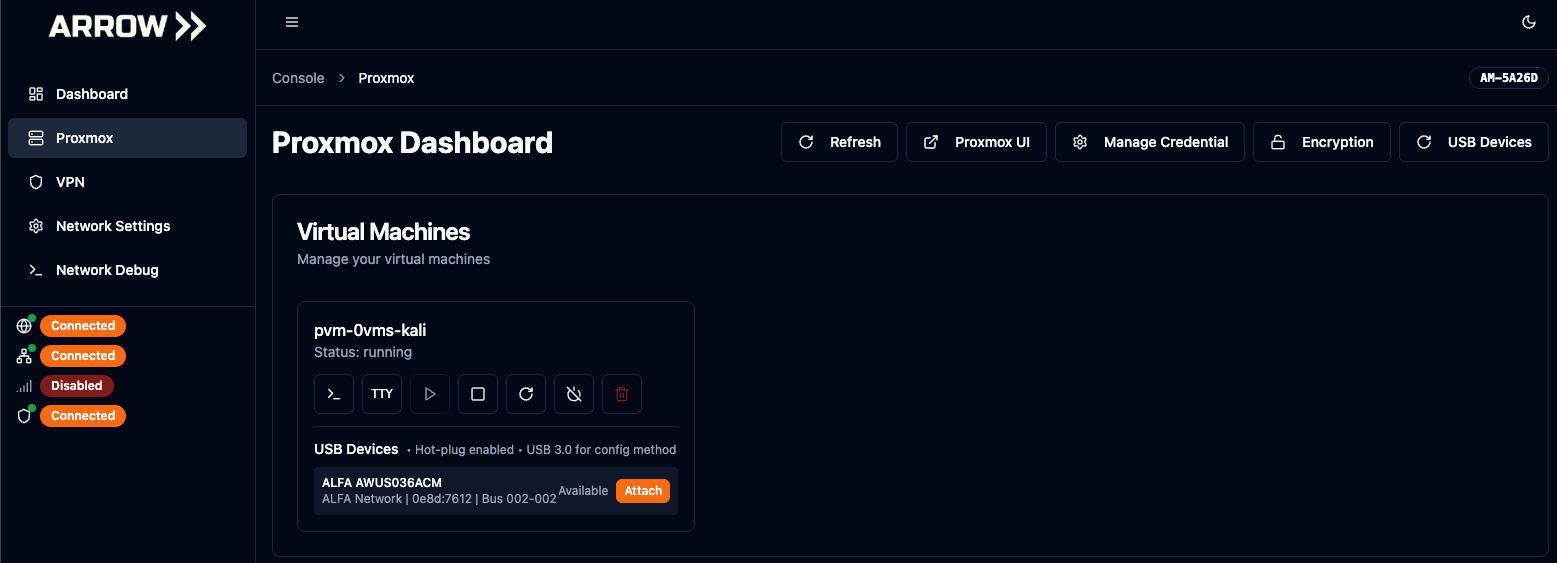 Deployed Virtual Machine w/ Wireless Card
Deployed Virtual Machine w/ Wireless Card
To access the virtual machine, follow the documentation provided in the Proxmox Virtual Machines section.
Device Completion Workflow
Section titled “Device Completion Workflow”When an engagement ends, the device completion process ensures proper cleanup and prepares devices for reuse.
Completing a Device Request
Section titled “Completing a Device Request”The completion process is triggered when a device request is marked as complete. This initiates automatic cleanup procedures:
- Return Verification: System checks if the return label was used and delivery was confirmed
- Cleanup Execution: Automated removal of device-specific configurations
- Device Release: Device is freed for the next engagement
Automatic Cleanup Actions
Section titled “Automatic Cleanup Actions”| Cleanup Action | Purpose | Timing |
|---|---|---|
| Remove NetBird Peers | Free VPN slots | On completion |
| Delete VPN Groups | Clean access control | On completion |
| Clear Device Organization | Make device available | On completion |
| Delete Device Settings | Fresh start for next use | On completion |
| Delete InfluxDB Metrics | Clean metric history | On completion (physical devices only) |
| Archive Device Serial | Audit trail | On completion |
| Refund Return Label | Cost recovery | On completion (if unused) |
Return Tracking
Section titled “Return Tracking”The system monitors return shipments through multiple methods:
- EasyPost Tracking: Automatic status updates for labels generated through the system
- Manual Tracking: Entry of tracking numbers for alternative carriers
- Delivery Confirmation: Timestamp capture when device arrives at warehouse
If the return label was not used (device returned via alternative method), the label can be refunded automatically.
Device Reuse
Section titled “Device Reuse”After completion, devices follow a reuse workflow:
- Organization Cleared: Device is disassociated from the previous organization
- Status Updated: Device marked as “available” in inventory
- Serial Archived: Previous engagement details preserved for audit trail
- Ready for Assignment: Device available for new device requests
This automated cleanup ensures devices are properly sanitized between engagements while maintaining a complete audit history.
Related Documentation
Section titled “Related Documentation”- Device Shipments - Shipping labels, tracking, and delivery workflows
- Auto-Inventory - Automated hardware inventory collection
- VPN Management - NetBird VPN configuration and management
- Device Requests - Creating and managing device requests